C语言实现DES+EBC+PKSC5/PKSC7加解密算法详解
创始人
2025-05-30 03:08:18
文章目录
- 一、前文
- 二、在线DES加密/解密工具
- 三、DES相关的基础知识
- 四、示例流程
- 五、全部源码
- 六、Gitee开源
一、前文
- DES算法通过Java/C#/Python等语言实现很简单,有现成的封装库。
- C语言实现则比较麻烦,找了半天才找到合适的算法实现。
- 本实例主要实现DES+EBC+PKSC5/PKSC7的加解密算法
- 源码开源:小康师兄 / DES (https://gitee.com/weijian.kang/DES)
二、在线DES加密/解密工具
- 在线DES加密/解密—LZL在线工具
- SSL在线工具-DES在线加解密
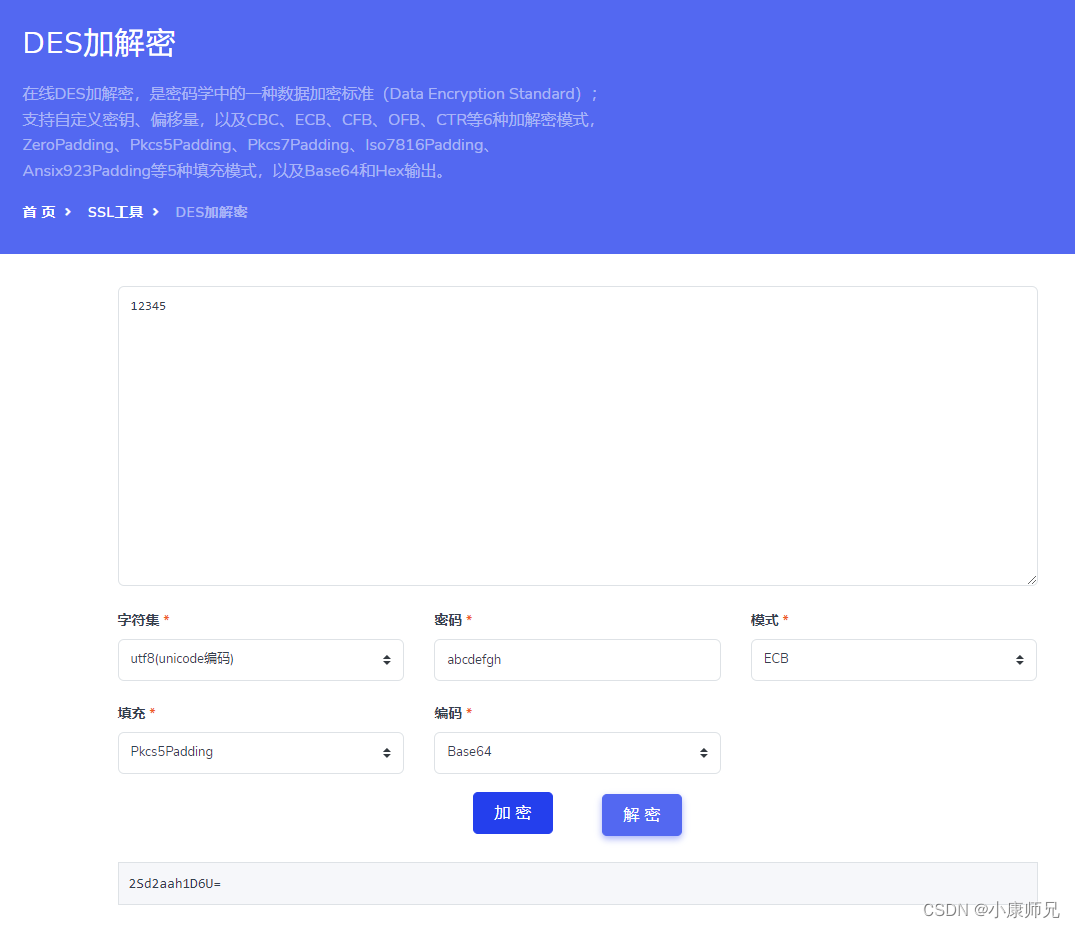
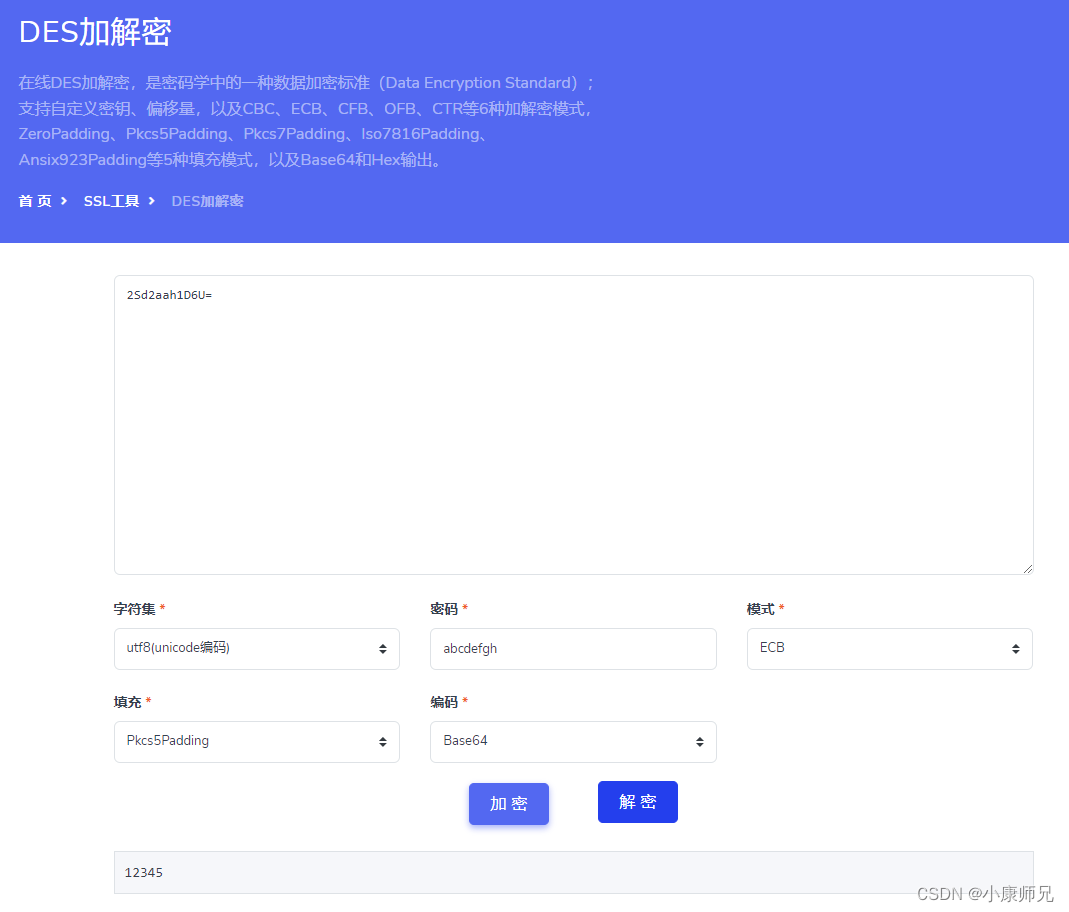
三、DES相关的基础知识
- DES全称为Data Encryption Standard,即数据加密标准,是一种使用密钥加密的块算法。
- 密钥长度是8个字节,数据块长度也是8个字节。
- 数据超过8个字节,则分组(块)加密。不足8个字节,则需要填充。
- 填充方式有很多种,比如
ZeroPadding、PKCS5Padding和PKCS7Padding等等ZeroPadding填充0数据,简单粗暴,但是缺点很明显,如果原始数据中就0数据,就无法判断是填充的数据,还是填充的数据。PKCS5Padding填充的数据==填充数据的长度。- 比如:
###,填充后:###55555; - 比如:
#####,填充后:#####333;
- 比如:
PKCS7Padding是为了支持AES,在PKCS5Padding上进行扩展。PKCS5Padding是针对8个字节块算法进行填充。PKCS7Padding则最大可以到255个字节的块算法。所以,对DES来说,PKCS5Padding和PKCS7Padding这两种填充方式是一样的。
- DES加密主要有两种
ECB和CBCECB:电子文本方式,相对简单CBC:密文分组连接方式,相对复杂,不易破解。需要增加参数:偏移向量IV。
四、示例流程
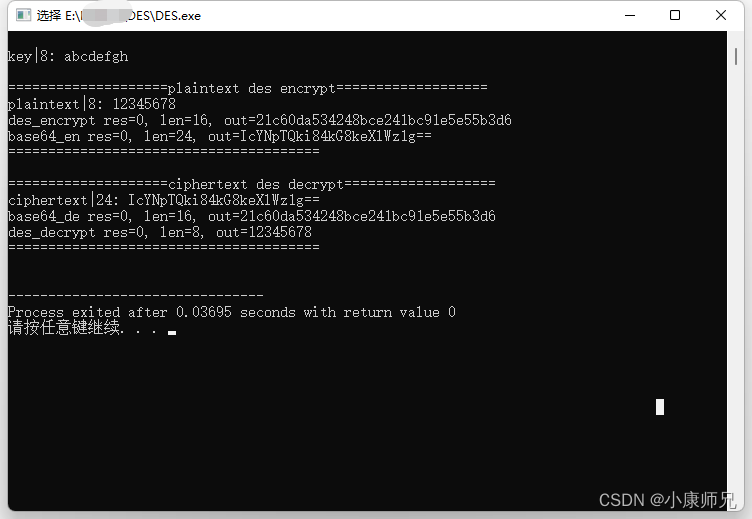
- 加密
- 明文plaintext——>des加密——>base64编码
- 解密
- 密文ciphertext——>base64解码——>des解密
Windows系统上可以选择VSCode搭建C语言开发环境,也可以选择Dev-C++集成开发工具
#include
#include
#include
#include
#include "stdio.h"
#include "stdlib.h"#include "crypto.h"//密钥
const unsigned char key[]="abcdefgh";
unsigned char key_len=strlen((const char*)key);//明文
const unsigned char plaintext[]="12345678";int main()
{int ret=0;int out_len=8;unsigned char *des_out, *base64_out, *out;printf("\r\nkey|%d: %s\r\n\r\n", key_len, key);printf("====================plaintext des encrypt===================\r\n");out_len = strlen((const char*)plaintext); printf("plaintext|%d: %s\r\n", out_len, plaintext);//des 加密ret=des_encrypt(DES_ECB, key, key_len, NULL, plaintext, &des_out, &out_len);printf("des_encrypt res=%d, len=%d, out=", ret, out_len);printHex(des_out, out_len);//base64 编码ret=base64_en(des_out, &base64_out, &out_len); printf("base64_en res=%d, len=%d, out=%s\r\n", ret, out_len, base64_out);free(base64_out); free(des_out); printf("=======================================\r\n\r\n");printf("====================ciphertext des decrypt===================\r\n");out_len = strlen((const char*)base64_out); printf("ciphertext|%d: %s\r\n", out_len, base64_out);//base64 解码ret=base64_de(base64_out, &out, &out_len); printf("base64_de res=%d, len=%d, out=", ret, out_len);printHex(out, out_len);//des 解密ret=des_decrypt(DES_ECB, key, key_len, NULL, out, &des_out, &out_len);des_out[out_len]='\0';printf("des_decrypt res=%d, len=%d, out=%s\r\n", ret, out_len, des_out);free(des_out); free(out); printf("=======================================\r\n\r\n");
}
五、全部源码
crypto.h
#ifndef __CRYPTO_H
#define __CRYPTO_Htypedef enum{DES_ECB =0,DES_CBC,DES3_ECB,DES3_CBC,
}CRYPTO_TYPE;typedef enum{RESULT_TYPE_BIN =0,//bin类型RESULT_TYPE_STR_UPPER,//HEX大写字符串RESULT_TYPE_STR_LOWER,//HEX小写字符串
}MD5_RESULT_TYPE;typedef enum{RESULT_OK = 0,RESULT_ERROR,
}CRYPTO_RESULT;#ifdef __cplusplus
extern "C" {
#endif/*DES 加密type[in]:加密方式key[in] 秘钥 des 固定8位 3des可为8位 16位 24位keyLen[in] 秘钥长度,des固定为8,3des可为8 16 24vi[in] 偏移 固定8位, CBC方式可用,ECB 为nullin[in] 待加密数据out[out] 加密后数据(需要free)len[in/out] 传入待加密数据长度,传出加密后数据长度return 是否成功
*/
CRYPTO_RESULT des_encrypt(CRYPTO_TYPE type, const unsigned char key[], unsigned char keyLen, const unsigned char vi[8], const unsigned char in[],unsigned char **out,int *len);/*DES 解密type[in]:解密方式key[in] 秘钥 des 固定8位 3des可为8位 16位 24位keyLen[in] 秘钥长度,des固定为8,3des可为8 16 24vi[in] 偏移 固定8位, CBC方式可用,ECB 为nullin[in] 待解密数据out[out] 解密后数据(需要free)len[in/out] 传入待解密数据长度,传出解密后数据长度return 是否成功
*/
CRYPTO_RESULT des_decrypt(CRYPTO_TYPE type, const unsigned char key[], unsigned char keyLen, const unsigned char vi[8], const unsigned char in[],unsigned char **out,int *len);/*BASE64编码type[in]:结果方式in[in] 待编码的数据out[out] 编码后数据(需要free)len[in/out] 传入编码要数据长度,传出编码后数据长度return 是否成功
*/CRYPTO_RESULT base64_en(const unsigned char in[],unsigned char **out,int *len);/*BASE64解码type[in]:结果方式in[in] 待解码的数据out[out] 解码后数据(需要free)len[in/out] 传入编码要数据长度,传出编码后数据长度return 是否成功
*/CRYPTO_RESULT base64_de(const unsigned char in[],unsigned char **out,int *len);void printHex(unsigned char *data , int len);#ifdef __cplusplus
}
#endif
#endifcrypto.c
#include
#include "stdio.h"
#include "stdlib.h"
#include "crypto.h"
#include "des.h"
#include "base64.h"void printHex(unsigned char *data , int len){int i = 0;for(i = 0; i < len; i++){//printf("%02X ",data[i]);printf("%02x",data[i]);}printf("\n");
}static unsigned char* pack_padding_pkcs5(const unsigned char in[], int *len){unsigned char paddNum = 8 - *len % 8;unsigned char *data = (unsigned char *)malloc(*len + paddNum);int i = 0;memset(data, 0, *len + paddNum);memcpy(data, in, *len);for (i = 0; i < paddNum; i++) {data[*len + i] = paddNum;}*len = *len + paddNum;return data;
}static unsigned char* unpack_padding_pkcs5(const unsigned char in[], int *len){unsigned char paddNum = in[*len - 1];if(paddNum > 8){*len = 0;return NULL;}*len = *len - paddNum;unsigned char *data = (unsigned char *)malloc(*len);memset(data, 0, *len);memcpy(data, in, *len );return data;
}CRYPTO_RESULT des_encrypt(CRYPTO_TYPE type, const unsigned char key[], unsigned char keyLen, const unsigned char vi[8], const unsigned char in[],unsigned char **out,int *len){unsigned char *data = pack_padding_pkcs5(in,len);*out = (unsigned char *)malloc(*len); if(type == DES_ECB || type == DES_CBC){mbedtls_des_context context;mbedtls_des_init(&context);mbedtls_des_setkey_enc(&context, key);if(type == DES_ECB){int i = 0;int num = *len / 8;for(i = 0; i < num; i++){mbedtls_des_crypt_ecb(&context, data + i * 8, *out + i * 8);}}else{unsigned char v[8] = {0};memcpy(v,vi,8);mbedtls_des_crypt_cbc(&context,MBEDTLS_DES_ENCRYPT,*len, v, data, *out);}}else if(type == DES3_ECB || type == DES3_CBC){mbedtls_des3_context context;if(keyLen != 8 && keyLen != 16 && keyLen != 24){return RESULT_ERROR;}unsigned char k[24] = {0};memcpy(k,key,keyLen);mbedtls_des3_init(&context);mbedtls_des3_set3key_enc(&context, k);if(type == DES3_ECB){int i = 0;int num = *len / 8;for(i = 0; i < num; i++){mbedtls_des3_crypt_ecb(&context, data + i * 8, *out + i * 8);}}else{unsigned char v[8] = {0};memcpy(v,vi,8);mbedtls_des3_crypt_cbc(&context,MBEDTLS_DES_ENCRYPT,*len, v, data, *out);}}free(data);return RESULT_OK;
}CRYPTO_RESULT des_decrypt(CRYPTO_TYPE type, const unsigned char key[], unsigned char keyLen, const unsigned char vi[8], const unsigned char in[],unsigned char **out,int *len){if(*len % 8){return RESULT_ERROR;}unsigned char *data = (unsigned char *)malloc(*len); if(type == DES_ECB || type == DES_CBC){mbedtls_des_context context;mbedtls_des_init(&context);mbedtls_des_setkey_dec(&context, key);if(type == DES_ECB){int i = 0;int num = *len / 8;for(i = 0; i < num; i++){mbedtls_des_crypt_ecb(&context, in + i * 8, data + i * 8);}}else{unsigned char v[8] = {0};memcpy(v,vi,8);mbedtls_des_crypt_cbc(&context,MBEDTLS_DES_DECRYPT,*len, v, in, data);}}else if(type == DES3_ECB || type == DES3_CBC){mbedtls_des3_context context;if(keyLen != 8 && keyLen != 16 && keyLen != 24){return RESULT_ERROR;}unsigned char k[24] = {0};memcpy(k,key,keyLen);mbedtls_des3_init(&context);mbedtls_des3_set3key_dec(&context, k);if(type == DES3_ECB){int i = 0;int num = *len / 8;for(i = 0; i < num; i++){mbedtls_des3_crypt_ecb(&context, in + i * 8, data + i * 8);}}else{unsigned char v[8] = {0};memcpy(v,vi,8);mbedtls_des3_crypt_cbc(&context,MBEDTLS_DES_DECRYPT,*len, v, in, data);}}*out = unpack_padding_pkcs5(data,len);free(data);if(*len == 0){return RESULT_ERROR;}return RESULT_OK;
}CRYPTO_RESULT base64_en(const unsigned char in[],unsigned char **out,int *len){unsigned char *encode_out;encode_out = (unsigned char*)malloc(BASE64_ENCODE_OUT_SIZE(*len));*len = base64_encode(in, *len, (char *)encode_out);if(*len > 0){*out = (unsigned char*)malloc(*len + 1);memset(*out,0,*len + 1);memcpy(*out,encode_out,*len);free(encode_out);return RESULT_OK;}else{*out = (unsigned char*)malloc(1);*out[0] = 0;*len = 0;free(encode_out);return RESULT_ERROR;}
}CRYPTO_RESULT base64_de(const unsigned char in[],unsigned char **out,int *len){unsigned char *decode_out;decode_out = (unsigned char*)malloc(BASE64_DECODE_OUT_SIZE(*len));*len = base64_decode((const char*)in, *len, decode_out);if(*len > 0){*out = (unsigned char*)malloc(*len);memset(*out,0,*len);memcpy(*out,decode_out,*len);free(decode_out);return RESULT_OK;}else{*out = (unsigned char*)malloc(1);*out[0] = 0;*len = 0;free(decode_out);return RESULT_ERROR;}
}
des.h
/*** \file des.h** \brief DES block cipher** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
/** Copyright (C) 2006-2015, ARM Limited, All Rights Reserved* SPDX-License-Identifier: Apache-2.0** Licensed under the Apache License, Version 2.0 (the "License"); you may* not use this file except in compliance with the License.* You may obtain a copy of the License at** http://www.apache.org/licenses/LICENSE-2.0** Unless required by applicable law or agreed to in writing, software* distributed under the License is distributed on an "AS IS" BASIS, WITHOUT* WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.* See the License for the specific language governing permissions and* limitations under the License.** This file is part of mbed TLS (https://tls.mbed.org)**/
#ifndef MBEDTLS_DES_H
#define MBEDTLS_DES_H#include
#include #define MBEDTLS_DES_ENCRYPT 1
#define MBEDTLS_DES_DECRYPT 0#define MBEDTLS_ERR_DES_INVALID_INPUT_LENGTH -0x0032 /**< The data input has an invalid length. */
#define MBEDTLS_ERR_DES_HW_ACCEL_FAILED -0x0033 /**< DES hardware accelerator failed. */#define MBEDTLS_DES_KEY_SIZE 8#ifdef __cplusplus
extern "C" {
#endif// Regular implementation
///*** \brief DES context structure** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
typedef struct mbedtls_des_context
{uint32_t sk[32]; /*!< DES subkeys */
}
mbedtls_des_context;/*** \brief Triple-DES context structure*/
typedef struct mbedtls_des3_context
{uint32_t sk[96]; /*!< 3DES subkeys */
}
mbedtls_des3_context;/*** \brief Initialize DES context** \param ctx DES context to be initialized** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
void mbedtls_des_init( mbedtls_des_context *ctx );/*** \brief Clear DES context** \param ctx DES context to be cleared** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
void mbedtls_des_free( mbedtls_des_context *ctx );/*** \brief Initialize Triple-DES context** \param ctx DES3 context to be initialized*/
void mbedtls_des3_init( mbedtls_des3_context *ctx );/*** \brief Clear Triple-DES context** \param ctx DES3 context to be cleared*/
void mbedtls_des3_free( mbedtls_des3_context *ctx );/*** \brief DES key schedule (56-bit, encryption)** \param ctx DES context to be initialized* \param key 8-byte secret key** \return 0** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
int mbedtls_des_setkey_enc( mbedtls_des_context *ctx, const unsigned char key[MBEDTLS_DES_KEY_SIZE] );/*** \brief DES key schedule (56-bit, decryption)** \param ctx DES context to be initialized* \param key 8-byte secret key** \return 0** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
int mbedtls_des_setkey_dec( mbedtls_des_context *ctx, const unsigned char key[MBEDTLS_DES_KEY_SIZE] );/*** \brief Triple-DES key schedule (112-bit, encryption)** \param ctx 3DES context to be initialized* \param key 16-byte secret key** \return 0*/
int mbedtls_des3_set2key_enc( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 2] );/*** \brief Triple-DES key schedule (112-bit, decryption)** \param ctx 3DES context to be initialized* \param key 16-byte secret key** \return 0*/
int mbedtls_des3_set2key_dec( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 2] );/*** \brief Triple-DES key schedule (168-bit, encryption)** \param ctx 3DES context to be initialized* \param key 24-byte secret key** \return 0*/
int mbedtls_des3_set3key_enc( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 3] );/*** \brief Triple-DES key schedule (168-bit, decryption)** \param ctx 3DES context to be initialized* \param key 24-byte secret key** \return 0*/
int mbedtls_des3_set3key_dec( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 3] );/*** \brief DES-ECB block encryption/decryption** \param ctx DES context* \param input 64-bit input block* \param output 64-bit output block** \return 0 if successful** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
int mbedtls_des_crypt_ecb( mbedtls_des_context *ctx,const unsigned char input[8],unsigned char output[8] );/*** \brief DES-CBC buffer encryption/decryption** \note Upon exit, the content of the IV is updated so that you can* call the function same function again on the following* block(s) of data and get the same result as if it was* encrypted in one call. This allows a "streaming" usage.* If on the other hand you need to retain the contents of the* IV, you should either save it manually or use the cipher* module instead.** \param ctx DES context* \param mode MBEDTLS_DES_ENCRYPT or MBEDTLS_DES_DECRYPT* \param length length of the input data* \param iv initialization vector (updated after use)* \param input buffer holding the input data* \param output buffer holding the output data** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
int mbedtls_des_crypt_cbc( mbedtls_des_context *ctx,int mode,size_t length,unsigned char iv[8],const unsigned char *input,unsigned char *output );/*** \brief 3DES-ECB block encryption/decryption** \param ctx 3DES context* \param input 64-bit input block* \param output 64-bit output block** \return 0 if successful*/
int mbedtls_des3_crypt_ecb( mbedtls_des3_context *ctx,const unsigned char input[8],unsigned char output[8] );/*** \brief 3DES-CBC buffer encryption/decryption** \note Upon exit, the content of the IV is updated so that you can* call the function same function again on the following* block(s) of data and get the same result as if it was* encrypted in one call. This allows a "streaming" usage.* If on the other hand you need to retain the contents of the* IV, you should either save it manually or use the cipher* module instead.** \param ctx 3DES context* \param mode MBEDTLS_DES_ENCRYPT or MBEDTLS_DES_DECRYPT* \param length length of the input data* \param iv initialization vector (updated after use)* \param input buffer holding the input data* \param output buffer holding the output data** \return 0 if successful, or MBEDTLS_ERR_DES_INVALID_INPUT_LENGTH*/
int mbedtls_des3_crypt_cbc( mbedtls_des3_context *ctx,int mode,size_t length,unsigned char iv[8],const unsigned char *input,unsigned char *output );/*** \brief Internal function for key expansion.* (Only exposed to allow overriding it,* see MBEDTLS_DES_SETKEY_ALT)** \param SK Round keys* \param key Base key** \warning DES is considered a weak cipher and its use constitutes a* security risk. We recommend considering stronger ciphers* instead.*/
void mbedtls_des_setkey( uint32_t SK[32],const unsigned char key[MBEDTLS_DES_KEY_SIZE] );#ifdef __cplusplus
}
#endif#endif /* des.h */ des.h
/** FIPS-46-3 compliant Triple-DES implementation** Copyright (C) 2006-2015, ARM Limited, All Rights Reserved* SPDX-License-Identifier: Apache-2.0** Licensed under the Apache License, Version 2.0 (the "License"); you may* not use this file except in compliance with the License.* You may obtain a copy of the License at** http://www.apache.org/licenses/LICENSE-2.0** Unless required by applicable law or agreed to in writing, software* distributed under the License is distributed on an "AS IS" BASIS, WITHOUT* WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.* See the License for the specific language governing permissions and* limitations under the License.** This file is part of mbed TLS (https://tls.mbed.org)*/
/** DES, on which TDES is based, was originally designed by Horst Feistel* at IBM in 1974, and was adopted as a standard by NIST (formerly NBS).** http://csrc.nist.gov/publications/fips/fips46-3/fips46-3.pdf*/#include "des.h"#include
#include /** 32-bit integer manipulation macros (big endian)*/
#ifndef GET_UINT32_BE
#define GET_UINT32_BE(n,b,i) \
{ \(n) = ( (uint32_t) (b)[(i) ] << 24 ) \| ( (uint32_t) (b)[(i) + 1] << 16 ) \| ( (uint32_t) (b)[(i) + 2] << 8 ) \| ( (uint32_t) (b)[(i) + 3] ); \
}
#endif#ifndef PUT_UINT32_BE
#define PUT_UINT32_BE(n,b,i) \
{ \(b)[(i) ] = (unsigned char) ( (n) >> 24 ); \(b)[(i) + 1] = (unsigned char) ( (n) >> 16 ); \(b)[(i) + 2] = (unsigned char) ( (n) >> 8 ); \(b)[(i) + 3] = (unsigned char) ( (n) ); \
}
#endif/** Expanded DES S-boxes*/
static const uint32_t SB1[64] =
{0x01010400, 0x00000000, 0x00010000, 0x01010404,0x01010004, 0x00010404, 0x00000004, 0x00010000,0x00000400, 0x01010400, 0x01010404, 0x00000400,0x01000404, 0x01010004, 0x01000000, 0x00000004,0x00000404, 0x01000400, 0x01000400, 0x00010400,0x00010400, 0x01010000, 0x01010000, 0x01000404,0x00010004, 0x01000004, 0x01000004, 0x00010004,0x00000000, 0x00000404, 0x00010404, 0x01000000,0x00010000, 0x01010404, 0x00000004, 0x01010000,0x01010400, 0x01000000, 0x01000000, 0x00000400,0x01010004, 0x00010000, 0x00010400, 0x01000004,0x00000400, 0x00000004, 0x01000404, 0x00010404,0x01010404, 0x00010004, 0x01010000, 0x01000404,0x01000004, 0x00000404, 0x00010404, 0x01010400,0x00000404, 0x01000400, 0x01000400, 0x00000000,0x00010004, 0x00010400, 0x00000000, 0x01010004
};static const uint32_t SB2[64] =
{0x80108020, 0x80008000, 0x00008000, 0x00108020,0x00100000, 0x00000020, 0x80100020, 0x80008020,0x80000020, 0x80108020, 0x80108000, 0x80000000,0x80008000, 0x00100000, 0x00000020, 0x80100020,0x00108000, 0x00100020, 0x80008020, 0x00000000,0x80000000, 0x00008000, 0x00108020, 0x80100000,0x00100020, 0x80000020, 0x00000000, 0x00108000,0x00008020, 0x80108000, 0x80100000, 0x00008020,0x00000000, 0x00108020, 0x80100020, 0x00100000,0x80008020, 0x80100000, 0x80108000, 0x00008000,0x80100000, 0x80008000, 0x00000020, 0x80108020,0x00108020, 0x00000020, 0x00008000, 0x80000000,0x00008020, 0x80108000, 0x00100000, 0x80000020,0x00100020, 0x80008020, 0x80000020, 0x00100020,0x00108000, 0x00000000, 0x80008000, 0x00008020,0x80000000, 0x80100020, 0x80108020, 0x00108000
};static const uint32_t SB3[64] =
{0x00000208, 0x08020200, 0x00000000, 0x08020008,0x08000200, 0x00000000, 0x00020208, 0x08000200,0x00020008, 0x08000008, 0x08000008, 0x00020000,0x08020208, 0x00020008, 0x08020000, 0x00000208,0x08000000, 0x00000008, 0x08020200, 0x00000200,0x00020200, 0x08020000, 0x08020008, 0x00020208,0x08000208, 0x00020200, 0x00020000, 0x08000208,0x00000008, 0x08020208, 0x00000200, 0x08000000,0x08020200, 0x08000000, 0x00020008, 0x00000208,0x00020000, 0x08020200, 0x08000200, 0x00000000,0x00000200, 0x00020008, 0x08020208, 0x08000200,0x08000008, 0x00000200, 0x00000000, 0x08020008,0x08000208, 0x00020000, 0x08000000, 0x08020208,0x00000008, 0x00020208, 0x00020200, 0x08000008,0x08020000, 0x08000208, 0x00000208, 0x08020000,0x00020208, 0x00000008, 0x08020008, 0x00020200
};static const uint32_t SB4[64] =
{0x00802001, 0x00002081, 0x00002081, 0x00000080,0x00802080, 0x00800081, 0x00800001, 0x00002001,0x00000000, 0x00802000, 0x00802000, 0x00802081,0x00000081, 0x00000000, 0x00800080, 0x00800001,0x00000001, 0x00002000, 0x00800000, 0x00802001,0x00000080, 0x00800000, 0x00002001, 0x00002080,0x00800081, 0x00000001, 0x00002080, 0x00800080,0x00002000, 0x00802080, 0x00802081, 0x00000081,0x00800080, 0x00800001, 0x00802000, 0x00802081,0x00000081, 0x00000000, 0x00000000, 0x00802000,0x00002080, 0x00800080, 0x00800081, 0x00000001,0x00802001, 0x00002081, 0x00002081, 0x00000080,0x00802081, 0x00000081, 0x00000001, 0x00002000,0x00800001, 0x00002001, 0x00802080, 0x00800081,0x00002001, 0x00002080, 0x00800000, 0x00802001,0x00000080, 0x00800000, 0x00002000, 0x00802080
};static const uint32_t SB5[64] =
{0x00000100, 0x02080100, 0x02080000, 0x42000100,0x00080000, 0x00000100, 0x40000000, 0x02080000,0x40080100, 0x00080000, 0x02000100, 0x40080100,0x42000100, 0x42080000, 0x00080100, 0x40000000,0x02000000, 0x40080000, 0x40080000, 0x00000000,0x40000100, 0x42080100, 0x42080100, 0x02000100,0x42080000, 0x40000100, 0x00000000, 0x42000000,0x02080100, 0x02000000, 0x42000000, 0x00080100,0x00080000, 0x42000100, 0x00000100, 0x02000000,0x40000000, 0x02080000, 0x42000100, 0x40080100,0x02000100, 0x40000000, 0x42080000, 0x02080100,0x40080100, 0x00000100, 0x02000000, 0x42080000,0x42080100, 0x00080100, 0x42000000, 0x42080100,0x02080000, 0x00000000, 0x40080000, 0x42000000,0x00080100, 0x02000100, 0x40000100, 0x00080000,0x00000000, 0x40080000, 0x02080100, 0x40000100
};static const uint32_t SB6[64] =
{0x20000010, 0x20400000, 0x00004000, 0x20404010,0x20400000, 0x00000010, 0x20404010, 0x00400000,0x20004000, 0x00404010, 0x00400000, 0x20000010,0x00400010, 0x20004000, 0x20000000, 0x00004010,0x00000000, 0x00400010, 0x20004010, 0x00004000,0x00404000, 0x20004010, 0x00000010, 0x20400010,0x20400010, 0x00000000, 0x00404010, 0x20404000,0x00004010, 0x00404000, 0x20404000, 0x20000000,0x20004000, 0x00000010, 0x20400010, 0x00404000,0x20404010, 0x00400000, 0x00004010, 0x20000010,0x00400000, 0x20004000, 0x20000000, 0x00004010,0x20000010, 0x20404010, 0x00404000, 0x20400000,0x00404010, 0x20404000, 0x00000000, 0x20400010,0x00000010, 0x00004000, 0x20400000, 0x00404010,0x00004000, 0x00400010, 0x20004010, 0x00000000,0x20404000, 0x20000000, 0x00400010, 0x20004010
};static const uint32_t SB7[64] =
{0x00200000, 0x04200002, 0x04000802, 0x00000000,0x00000800, 0x04000802, 0x00200802, 0x04200800,0x04200802, 0x00200000, 0x00000000, 0x04000002,0x00000002, 0x04000000, 0x04200002, 0x00000802,0x04000800, 0x00200802, 0x00200002, 0x04000800,0x04000002, 0x04200000, 0x04200800, 0x00200002,0x04200000, 0x00000800, 0x00000802, 0x04200802,0x00200800, 0x00000002, 0x04000000, 0x00200800,0x04000000, 0x00200800, 0x00200000, 0x04000802,0x04000802, 0x04200002, 0x04200002, 0x00000002,0x00200002, 0x04000000, 0x04000800, 0x00200000,0x04200800, 0x00000802, 0x00200802, 0x04200800,0x00000802, 0x04000002, 0x04200802, 0x04200000,0x00200800, 0x00000000, 0x00000002, 0x04200802,0x00000000, 0x00200802, 0x04200000, 0x00000800,0x04000002, 0x04000800, 0x00000800, 0x00200002
};static const uint32_t SB8[64] =
{0x10001040, 0x00001000, 0x00040000, 0x10041040,0x10000000, 0x10001040, 0x00000040, 0x10000000,0x00040040, 0x10040000, 0x10041040, 0x00041000,0x10041000, 0x00041040, 0x00001000, 0x00000040,0x10040000, 0x10000040, 0x10001000, 0x00001040,0x00041000, 0x00040040, 0x10040040, 0x10041000,0x00001040, 0x00000000, 0x00000000, 0x10040040,0x10000040, 0x10001000, 0x00041040, 0x00040000,0x00041040, 0x00040000, 0x10041000, 0x00001000,0x00000040, 0x10040040, 0x00001000, 0x00041040,0x10001000, 0x00000040, 0x10000040, 0x10040000,0x10040040, 0x10000000, 0x00040000, 0x10001040,0x00000000, 0x10041040, 0x00040040, 0x10000040,0x10040000, 0x10001000, 0x10001040, 0x00000000,0x10041040, 0x00041000, 0x00041000, 0x00001040,0x00001040, 0x00040040, 0x10000000, 0x10041000
};/** PC1: left and right halves bit-swap*/
static const uint32_t LHs[16] =
{0x00000000, 0x00000001, 0x00000100, 0x00000101,0x00010000, 0x00010001, 0x00010100, 0x00010101,0x01000000, 0x01000001, 0x01000100, 0x01000101,0x01010000, 0x01010001, 0x01010100, 0x01010101
};static const uint32_t RHs[16] =
{0x00000000, 0x01000000, 0x00010000, 0x01010000,0x00000100, 0x01000100, 0x00010100, 0x01010100,0x00000001, 0x01000001, 0x00010001, 0x01010001,0x00000101, 0x01000101, 0x00010101, 0x01010101,
};/** Initial Permutation macro*/
#define DES_IP(X,Y) \
{ \T = ((X >> 4) ^ Y) & 0x0F0F0F0F; Y ^= T; X ^= (T << 4); \T = ((X >> 16) ^ Y) & 0x0000FFFF; Y ^= T; X ^= (T << 16); \T = ((Y >> 2) ^ X) & 0x33333333; X ^= T; Y ^= (T << 2); \T = ((Y >> 8) ^ X) & 0x00FF00FF; X ^= T; Y ^= (T << 8); \Y = ((Y << 1) | (Y >> 31)) & 0xFFFFFFFF; \T = (X ^ Y) & 0xAAAAAAAA; Y ^= T; X ^= T; \X = ((X << 1) | (X >> 31)) & 0xFFFFFFFF; \
}/** Final Permutation macro*/
#define DES_FP(X,Y) \
{ \X = ((X << 31) | (X >> 1)) & 0xFFFFFFFF; \T = (X ^ Y) & 0xAAAAAAAA; X ^= T; Y ^= T; \Y = ((Y << 31) | (Y >> 1)) & 0xFFFFFFFF; \T = ((Y >> 8) ^ X) & 0x00FF00FF; X ^= T; Y ^= (T << 8); \T = ((Y >> 2) ^ X) & 0x33333333; X ^= T; Y ^= (T << 2); \T = ((X >> 16) ^ Y) & 0x0000FFFF; Y ^= T; X ^= (T << 16); \T = ((X >> 4) ^ Y) & 0x0F0F0F0F; Y ^= T; X ^= (T << 4); \
}/** DES round macro*/
#define DES_ROUND(X,Y) \
{ \T = *SK++ ^ X; \Y ^= SB8[ (T ) & 0x3F ] ^ \SB6[ (T >> 8) & 0x3F ] ^ \SB4[ (T >> 16) & 0x3F ] ^ \SB2[ (T >> 24) & 0x3F ]; \\T = *SK++ ^ ((X << 28) | (X >> 4)); \Y ^= SB7[ (T ) & 0x3F ] ^ \SB5[ (T >> 8) & 0x3F ] ^ \SB3[ (T >> 16) & 0x3F ] ^ \SB1[ (T >> 24) & 0x3F ]; \
}#define SWAP(a,b) { uint32_t t = a; a = b; b = t; t = 0; }void mbedtls_des_init( mbedtls_des_context *ctx )
{memset( ctx, 0, sizeof( mbedtls_des_context ) );
}void mbedtls_des_free( mbedtls_des_context *ctx )
{if( ctx == NULL )return;memset( ctx, 0, sizeof( mbedtls_des_context ) );
}void mbedtls_des3_init( mbedtls_des3_context *ctx )
{memset( ctx, 0, sizeof( mbedtls_des3_context ) );
}void mbedtls_des3_free( mbedtls_des3_context *ctx )
{if( ctx == NULL )return;memset( ctx, 0, sizeof( mbedtls_des3_context ) );
}void mbedtls_des_setkey( uint32_t SK[32], const unsigned char key[MBEDTLS_DES_KEY_SIZE] )
{int i;uint32_t X, Y, T;GET_UINT32_BE( X, key, 0 );GET_UINT32_BE( Y, key, 4 );/** Permuted Choice 1*/T = ((Y >> 4) ^ X) & 0x0F0F0F0F; X ^= T; Y ^= (T << 4);T = ((Y ) ^ X) & 0x10101010; X ^= T; Y ^= (T );X = (LHs[ (X ) & 0xF] << 3) | (LHs[ (X >> 8) & 0xF ] << 2)| (LHs[ (X >> 16) & 0xF] << 1) | (LHs[ (X >> 24) & 0xF ] )| (LHs[ (X >> 5) & 0xF] << 7) | (LHs[ (X >> 13) & 0xF ] << 6)| (LHs[ (X >> 21) & 0xF] << 5) | (LHs[ (X >> 29) & 0xF ] << 4);Y = (RHs[ (Y >> 1) & 0xF] << 3) | (RHs[ (Y >> 9) & 0xF ] << 2)| (RHs[ (Y >> 17) & 0xF] << 1) | (RHs[ (Y >> 25) & 0xF ] )| (RHs[ (Y >> 4) & 0xF] << 7) | (RHs[ (Y >> 12) & 0xF ] << 6)| (RHs[ (Y >> 20) & 0xF] << 5) | (RHs[ (Y >> 28) & 0xF ] << 4);X &= 0x0FFFFFFF;Y &= 0x0FFFFFFF;/** calculate subkeys*/for( i = 0; i < 16; i++ ){if( i < 2 || i == 8 || i == 15 ){X = ((X << 1) | (X >> 27)) & 0x0FFFFFFF;Y = ((Y << 1) | (Y >> 27)) & 0x0FFFFFFF;}else{X = ((X << 2) | (X >> 26)) & 0x0FFFFFFF;Y = ((Y << 2) | (Y >> 26)) & 0x0FFFFFFF;}*SK++ = ((X << 4) & 0x24000000) | ((X << 28) & 0x10000000)| ((X << 14) & 0x08000000) | ((X << 18) & 0x02080000)| ((X << 6) & 0x01000000) | ((X << 9) & 0x00200000)| ((X >> 1) & 0x00100000) | ((X << 10) & 0x00040000)| ((X << 2) & 0x00020000) | ((X >> 10) & 0x00010000)| ((Y >> 13) & 0x00002000) | ((Y >> 4) & 0x00001000)| ((Y << 6) & 0x00000800) | ((Y >> 1) & 0x00000400)| ((Y >> 14) & 0x00000200) | ((Y ) & 0x00000100)| ((Y >> 5) & 0x00000020) | ((Y >> 10) & 0x00000010)| ((Y >> 3) & 0x00000008) | ((Y >> 18) & 0x00000004)| ((Y >> 26) & 0x00000002) | ((Y >> 24) & 0x00000001);*SK++ = ((X << 15) & 0x20000000) | ((X << 17) & 0x10000000)| ((X << 10) & 0x08000000) | ((X << 22) & 0x04000000)| ((X >> 2) & 0x02000000) | ((X << 1) & 0x01000000)| ((X << 16) & 0x00200000) | ((X << 11) & 0x00100000)| ((X << 3) & 0x00080000) | ((X >> 6) & 0x00040000)| ((X << 15) & 0x00020000) | ((X >> 4) & 0x00010000)| ((Y >> 2) & 0x00002000) | ((Y << 8) & 0x00001000)| ((Y >> 14) & 0x00000808) | ((Y >> 9) & 0x00000400)| ((Y ) & 0x00000200) | ((Y << 7) & 0x00000100)| ((Y >> 7) & 0x00000020) | ((Y >> 3) & 0x00000011)| ((Y << 2) & 0x00000004) | ((Y >> 21) & 0x00000002);}
}/** DES key schedule (56-bit, encryption)*/
int mbedtls_des_setkey_enc( mbedtls_des_context *ctx, const unsigned char key[MBEDTLS_DES_KEY_SIZE] )
{mbedtls_des_setkey( ctx->sk, key );return( 0 );
}/** DES key schedule (56-bit, decryption)*/
int mbedtls_des_setkey_dec( mbedtls_des_context *ctx, const unsigned char key[MBEDTLS_DES_KEY_SIZE] )
{int i;mbedtls_des_setkey( ctx->sk, key );for( i = 0; i < 16; i += 2 ){SWAP( ctx->sk[i ], ctx->sk[30 - i] );SWAP( ctx->sk[i + 1], ctx->sk[31 - i] );}return( 0 );
}static void des3_set2key( uint32_t esk[96],uint32_t dsk[96],const unsigned char key[MBEDTLS_DES_KEY_SIZE*2] )
{int i;mbedtls_des_setkey( esk, key );mbedtls_des_setkey( dsk + 32, key + 8 );for( i = 0; i < 32; i += 2 ){dsk[i ] = esk[30 - i];dsk[i + 1] = esk[31 - i];esk[i + 32] = dsk[62 - i];esk[i + 33] = dsk[63 - i];esk[i + 64] = esk[i ];esk[i + 65] = esk[i + 1];dsk[i + 64] = dsk[i ];dsk[i + 65] = dsk[i + 1];}
}/** Triple-DES key schedule (112-bit, encryption)*/
int mbedtls_des3_set2key_enc( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 2] )
{uint32_t sk[96];des3_set2key( ctx->sk, sk, key );memset( sk, 0, sizeof( sk ) );return( 0 );
}/** Triple-DES key schedule (112-bit, decryption)*/
int mbedtls_des3_set2key_dec( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 2] )
{uint32_t sk[96];des3_set2key( sk, ctx->sk, key );memset( sk, 0, sizeof( sk ) );return( 0 );
}static void des3_set3key( uint32_t esk[96],uint32_t dsk[96],const unsigned char key[24] )
{int i;mbedtls_des_setkey( esk, key );mbedtls_des_setkey( dsk + 32, key + 8 );mbedtls_des_setkey( esk + 64, key + 16 );for( i = 0; i < 32; i += 2 ){dsk[i ] = esk[94 - i];dsk[i + 1] = esk[95 - i];esk[i + 32] = dsk[62 - i];esk[i + 33] = dsk[63 - i];dsk[i + 64] = esk[30 - i];dsk[i + 65] = esk[31 - i];}
}/** Triple-DES key schedule (168-bit, encryption)*/
int mbedtls_des3_set3key_enc( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 3] )
{uint32_t sk[96];des3_set3key( ctx->sk, sk, key );memset( sk, 0, sizeof( sk ) );return( 0 );
}/** Triple-DES key schedule (168-bit, decryption)*/
int mbedtls_des3_set3key_dec( mbedtls_des3_context *ctx,const unsigned char key[MBEDTLS_DES_KEY_SIZE * 3] )
{uint32_t sk[96];des3_set3key( sk, ctx->sk, key );memset( sk, 0, sizeof( sk ) );return( 0 );
}/** DES-ECB block encryption/decryption*/
int mbedtls_des_crypt_ecb( mbedtls_des_context *ctx,const unsigned char input[8],unsigned char output[8] )
{int i;uint32_t X, Y, T, *SK;SK = ctx->sk;GET_UINT32_BE( X, input, 0 );GET_UINT32_BE( Y, input, 4 );DES_IP( X, Y );for( i = 0; i < 8; i++ ){DES_ROUND( Y, X );DES_ROUND( X, Y );}DES_FP( Y, X );PUT_UINT32_BE( Y, output, 0 );PUT_UINT32_BE( X, output, 4 );return( 0 );
}/** DES-CBC buffer encryption/decryption*/
int mbedtls_des_crypt_cbc( mbedtls_des_context *ctx,int mode,size_t length,unsigned char iv[8],const unsigned char *input,unsigned char *output )
{int i;unsigned char temp[8];if( length % 8 )return( MBEDTLS_ERR_DES_INVALID_INPUT_LENGTH );if( mode == MBEDTLS_DES_ENCRYPT ){while( length > 0 ){for( i = 0; i < 8; i++ )output[i] = (unsigned char)( input[i] ^ iv[i] );mbedtls_des_crypt_ecb( ctx, output, output );memcpy( iv, output, 8 );input += 8;output += 8;length -= 8;}}else /* MBEDTLS_DES_DECRYPT */{while( length > 0 ){memcpy( temp, input, 8 );mbedtls_des_crypt_ecb( ctx, input, output );for( i = 0; i < 8; i++ )output[i] = (unsigned char)( output[i] ^ iv[i] );memcpy( iv, temp, 8 );input += 8;output += 8;length -= 8;}}return( 0 );
}/** 3DES-ECB block encryption/decryption*/
int mbedtls_des3_crypt_ecb( mbedtls_des3_context *ctx,const unsigned char input[8],unsigned char output[8] )
{int i;uint32_t X, Y, T, *SK;SK = ctx->sk;GET_UINT32_BE( X, input, 0 );GET_UINT32_BE( Y, input, 4 );DES_IP( X, Y );for( i = 0; i < 8; i++ ){DES_ROUND( Y, X );DES_ROUND( X, Y );}for( i = 0; i < 8; i++ ){DES_ROUND( X, Y );DES_ROUND( Y, X );}for( i = 0; i < 8; i++ ){DES_ROUND( Y, X );DES_ROUND( X, Y );}DES_FP( Y, X );PUT_UINT32_BE( Y, output, 0 );PUT_UINT32_BE( X, output, 4 );return( 0 );
}/** 3DES-CBC buffer encryption/decryption*/
int mbedtls_des3_crypt_cbc( mbedtls_des3_context *ctx,int mode,size_t length,unsigned char iv[8],const unsigned char *input,unsigned char *output )
{int i;unsigned char temp[8];if( length % 8 )return( MBEDTLS_ERR_DES_INVALID_INPUT_LENGTH );if( mode == MBEDTLS_DES_ENCRYPT ){while( length > 0 ){for( i = 0; i < 8; i++ )output[i] = (unsigned char)( input[i] ^ iv[i] );mbedtls_des3_crypt_ecb( ctx, output, output );memcpy( iv, output, 8 );input += 8;output += 8;length -= 8;}}else /* MBEDTLS_DES_DECRYPT */{while( length > 0 ){memcpy( temp, input, 8 );mbedtls_des3_crypt_ecb( ctx, input, output );for( i = 0; i < 8; i++ )output[i] = (unsigned char)( output[i] ^ iv[i] );memcpy( iv, temp, 8 );input += 8;output += 8;length -= 8;}}return( 0 );
}
base64.h
#ifndef BASE64_H
#define BASE64_H#define BASE64_ENCODE_OUT_SIZE(s) ((unsigned int)((((s) + 2) / 3) * 4 + 1))
#define BASE64_DECODE_OUT_SIZE(s) ((unsigned int)(((s) / 4) * 3))#ifdef __cplusplus
extern "C" {
#endif/** out is null-terminated encode string.* return values is out length, exclusive terminating `\0'*/
unsigned int
base64_encode(const unsigned char *in, unsigned int inlen, char *out);/** return values is out length*/
unsigned int
base64_decode(const char *in, unsigned int inlen, unsigned char *out);#ifdef __cplusplus
}
#endif#endif /* BASE64_H */base64.c
/* This is a public domain base64 implementation written by WEI Zhicheng. */#include "base64.h"#define BASE64_PAD '='/* BASE 64 encode table */
static const char base64en[] = {'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H','I', 'J', 'K', 'L', 'M', 'N', 'O', 'P','Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X','Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f','g', 'h', 'i', 'j', 'k', 'l', 'm', 'n','o', 'p', 'q', 'r', 's', 't', 'u', 'v','w', 'x', 'y', 'z', '0', '1', '2', '3','4', '5', '6', '7', '8', '9', '+', '/',
};/* ASCII order for BASE 64 decode, 255 in unused character */
static const unsigned char base64de[] = {/* nul, soh, stx, etx, eot, enq, ack, bel, */255, 255, 255, 255, 255, 255, 255, 255,/* bs, ht, nl, vt, np, cr, so, si, */255, 255, 255, 255, 255, 255, 255, 255,/* dle, dc1, dc2, dc3, dc4, nak, syn, etb, */255, 255, 255, 255, 255, 255, 255, 255,/* can, em, sub, esc, fs, gs, rs, us, */255, 255, 255, 255, 255, 255, 255, 255,/* sp, '!', '"', '#', '$', '%', '&', ''', */255, 255, 255, 255, 255, 255, 255, 255,/* '(', ')', '*', '+', ',', '-', '.', '/', */255, 255, 255, 62, 255, 255, 255, 63,/* '0', '1', '2', '3', '4', '5', '6', '7', */52, 53, 54, 55, 56, 57, 58, 59,/* '8', '9', ':', ';', '<', '=', '>', '?', */60, 61, 255, 255, 255, 255, 255, 255,/* '@', 'A', 'B', 'C', 'D', 'E', 'F', 'G', */255, 0, 1, 2, 3, 4, 5, 6,/* 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', */7, 8, 9, 10, 11, 12, 13, 14,/* 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', */15, 16, 17, 18, 19, 20, 21, 22,/* 'X', 'Y', 'Z', '[', '\', ']', '^', '_', */23, 24, 25, 255, 255, 255, 255, 255,/* '`', 'a', 'b', 'c', 'd', 'e', 'f', 'g', */255, 26, 27, 28, 29, 30, 31, 32,/* 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', */33, 34, 35, 36, 37, 38, 39, 40,/* 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', */41, 42, 43, 44, 45, 46, 47, 48,/* 'x', 'y', 'z', '{', '|', '}', '~', del, */49, 50, 51, 255, 255, 255, 255, 255
};unsigned int
base64_encode(const unsigned char *in, unsigned int inlen, char *out)
{int s;unsigned int i;unsigned int j;unsigned char c;unsigned char l;s = 0;l = 0;for (i = j = 0; i < inlen; i++) {c = in[i];switch (s) {case 0:s = 1;out[j++] = base64en[(c >> 2) & 0x3F];break;case 1:s = 2;out[j++] = base64en[((l & 0x3) << 4) | ((c >> 4) & 0xF)];break;case 2:s = 0;out[j++] = base64en[((l & 0xF) << 2) | ((c >> 6) & 0x3)];out[j++] = base64en[c & 0x3F];break;}l = c;}switch (s) {case 1:out[j++] = base64en[(l & 0x3) << 4];out[j++] = BASE64_PAD;out[j++] = BASE64_PAD;break;case 2:out[j++] = base64en[(l & 0xF) << 2];out[j++] = BASE64_PAD;break;}out[j] = 0;return j;
}unsigned int
base64_decode(const char *in, unsigned int inlen, unsigned char *out)
{unsigned int i;unsigned int j;unsigned char c;if (inlen & 0x3) {return 0;}for (i = j = 0; i < inlen; i++) {if (in[i] == BASE64_PAD) {break;}if (in[i] < 0) {return 0;}c = base64de[in[i]];if (c == 255) {return 0;}switch (i & 0x3) {case 0:out[j] = (c << 2) & 0xFF;break;case 1:out[j++] |= (c >> 4) & 0x3;out[j] = (c & 0xF) << 4; break;case 2:out[j++] |= (c >> 2) & 0xF;out[j] = (c & 0x3) << 6;break;case 3:out[j++] |= c;break;}}out[j] = '\0';return j;
}六、Gitee开源
- 小康师兄 / DES (https://gitee.com/weijian.kang/DES)
觉得好,就一键三连呗(点赞+收藏+关注)
相关内容
热门资讯
上市公司同仁堂澄清:南极磷虾油...
中经记者 晏国文 卢志坤 北京报道(同仁堂、同仁堂集团与涉事企业关系图。 天眼查/图)12月17日晚...
沐曦股份单日盈利封王
2025.12.17本文字数:2487,阅读时长大约4分钟作者 |第一财经 魏中原12月17日,国产...
冲刺“大模型第一股”!Mini...
12月17日,澎湃新闻记者从多位知情人士处了解到,智谱、MiniMax(稀宇科技)两家AI大模型独角...
主业疲软、投资“撑场”:CRO...
本报(chinatimes.net.cn)记者赵文娟 于娜 北京报道国内临床CRO龙头企业泰格医药(...
同仁堂回应“南极磷虾油产品”报...
同仁堂发布澄清公告。12月17日晚间,北京同仁堂股份有限公司(同仁堂,600085.SH)发布关于相...
